I am carrying out research on cyber and physical security technologies, as well as in the area where the two overlap.
Summary of research
Cyber-physical security of autonomous vehicles
 A cyber-physical system is vulnerable where cyber and physical spaces overlap, as attacks lead to physical actions inconsistent with system states and goals. Monitoring its physical characteristics improves threat detection accuracy and reduces detection latency.
A cyber-physical system is vulnerable where cyber and physical spaces overlap, as attacks lead to physical actions inconsistent with system states and goals. Monitoring its physical characteristics improves threat detection accuracy and reduces detection latency.
Human-as-a-Security-Sensor (HaaS)
 We have introduced the paradigm of detecting security threats by empowering users to act as human sensors. HaaS breaks away from the tradition of system-specific technical security measures and challenges the misconception that users are the weakest link. People are invaluable threat detectors in their organisations, especially for deception-based threats that defeat technical security measures.
We have introduced the paradigm of detecting security threats by empowering users to act as human sensors. HaaS breaks away from the tradition of system-specific technical security measures and challenges the misconception that users are the weakest link. People are invaluable threat detectors in their organisations, especially for deception-based threats that defeat technical security measures.
Deep learning and computation offloading for threat detection
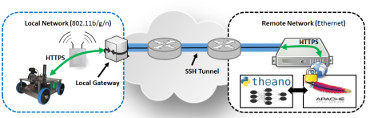
As cyber-physical and Internet of Things systems typically afford limited processing resources, threat detection is usually based on lightweight machine learning. This limitation can be lifted with computational offloading. The increased processing resources available in this manner allow access to more advanced approaches, such as deep learning which achieves greater energy efficiency and high accuracy more consistently.
Detecting cyber threats in smart homes
Home is a safe haven to experience privacy and control, personal autonomy and integrity. In the COCOON project, we study the emotional impact of cyber-physical threats in smart homes. We also designed detection technologies that are dynamically adjusted in accordance with the user's tolerance for false positives Vs. false negatives. You can downwload MAGPIE, our open-source complete intrusion detection system for smart homes.
Publications
C47 - Sakshyam Panda, Emmanouil Panaousis, George Loukas, Konstantinos Kentrotis. Privacy Impact Assessment of Cyber Attacks on Connected and Autonomous Vehicles, Proceedings of the 18th International Conference on Availability, Reliability and Security, August 2023.
J39 - Emily Kate Parsons, Emmanouil Panaousis, George Loukas, Georgia Sakellari. A Survey on Cyber Risk Management for the Internet of Things. Applied Sciences, 13(15), 2023.
J38 - Yunxiao Zhang, Pasquale Malacaria, Emmanouil Panaousis, George Loukas. CROSS: A Framework for Cyber Risk Optimisation in Smart Homes. Computers and Security, Elsevier, 2023. (IF: 5.1)
J37 - Antonia Nisioti, George Loukas, Alexios Mylonas, Emmanouil Panaousis. Forensics for multi-stage cyber incidents: Survey and future directions. Forensic Science International: Digital Investigation, Elsevier, 2023. (IF: 1.8)
J36 - Blessing Odeleye, George Loukas, Ryan Heartfield, Georgia Sakellari, Emmanouil Panaousis, Fotios Spyridonis. Virtually Secure: A taxonomic assessment of cybersecurity challenges in virtual reality environments. Computers & Security, Elsevier, 2022. (IF: 5.1)
J35 - S. Panda, S. Rass, S. Moschoyiannis, K. Liang, G. Loukas, E. Panaousis. HoneyCar: A Framework to Configure HoneypotVulnerabilities on the Internet of Vehicles. IEEE Access, 10, 2022. (IF: 3.4)
C46 - Emma Scott, Sakshyam Panda, George Loukas, Emmanouil Panaousis. Optimising user security recommendations for AI-powered smart-homes. 5th IEEE Conference on Dependable and Secure Computing, 2022.
J34 - George Loukas, San Murugesan, SJ Andriole. Information Hygiene: The Fight Against the Misinformation “Infodemic”. IT Professional, 24 (2):16-18, 2022.
C45 - Blessing Odeleye, George Loukas, Ryan Heartfield, Fotios Spyridonis. Detecting framerate-oriented cyber attacks on user experience in virtual reality. VR4Sec: 1st International Workshop on Security for XR and XR for Security, August 2021.
J33 - Panagiotis Kasnesis, Ryan Heartfield, Xing Liang, Lazaros Toumanidis, Georgia Sakellari, Charalampos Patrikakis, George Loukas. Transformer-based identification of stochastic information cascades in social networks using text and image similarity. Applied Soft Computing, Elsevier, 2021.
J32 - Sanja Budimir, Johnny Fontaine, Nicole MA Huijts, Antal Haans, George Loukas, Etienne Roesch. Emotional reactions to cybersecurity breach situations: A Scenario-based Survey Study. Journal of Medical Internet Research, 2021.
J31 - Antonia Nisioti, George Loukas, Aron Laszka, Emmanouil Panaousis. Data-Driven Decision Support for Optimizing Cyber Forensic Investigations. IEEE Transactions on Information Forensics and Security, 2021.
J30 - Ryan Heartfield, George Loukas, Anatolij Bezemskij, Emmanouil Panaousis. Self-configurable cyber-physical intrusion detection for smart homes using reinforcement learning. IEEE Transactions on Information Forensics and Security, 2020.
C44 - Emily Kate Parsons, Emmanouil Panaousis, George Loukas. How secure is home: assessing human susceptibility to IoT threats. 24th Pan-Hellenic Conference on Informatics, 2020.
J29 - S. Budimir, J. Fontaine, N. Huijts, A. Haans, G. Loukas, I. Ras, E. Roesch. Emotions, personality, and psychopathology of cybersecurity breach victims. Journal of Psychosomatic Research, 133, 2020.
J28 - Jiahui Chen, Jie Ling, Jianting Ning, Emmanouil Panaousis, George Loukas, Kaitai Liang, Jiageng Chen. Post quantum proxy signature scheme based on the multivariate public key cryptographic signature. International Journal of Distributed Sensor Networks, 16(4), 2020.
J27 - George Theodorakopoulos, Emmanouil Panaousis, Kaitai Liang, George Loukas. On-the-fly Privacy for Location Histograms. IEEE Transactions on Dependable and Secure Computing (TDSC), (IF: 7.3), IEEE, 19: 566–578, 2022.
C43 - Panagiotis Kasnesis, Ryan Heartfield, Lazaros Toumanidis, Xing Liang, George Loukas, Charalampos Patrikakis. A prototype deep learning paraphrase identification service for discovering information cascades in social networks. IEEE International Conference on Multimedia and Expo (ICME), IEEE, 2020.
C42 - Ilias Siniosoglou, Georgios Efstathopoulos, Dimitrios Pliatsios, Ioannis Moscholios, Antonios Sarigiannidis, Georgia Sakellari, Georgios Loukas, Panagiotis Sarigiannidis. NeuralPot: An Industrial Honeypot Implementation Based On Convolutional Neural Networks. IEEE Symposium on Computers and Communications (ISCC), IEEE, 2020.
J26 - George Loukas, Charalampos Z. Patrikakis, Linda R. Wilbanks. Digital deception: Cyber fraud and online misinformation. IT Professional, 2020.
J25 - Jiahui Chen, Jie Ling, Jianting Ning, Emmanouil Panaousis, George Loukas, Kaitai Liang, Jiageng Chen. Post quantum proxy signature scheme based on the multivariate public key cryptographic signature, International Journal of Distributed Sensor Networks 16 (4), 2020.
J24 - Ali Jaddoa, Georgia Sakellari, Emmanouil Panaousis, George Loukas and Panagiotis Sarigiannidis. Dynamic decision support for resource offloading in heterogeneous Internet of Things environments. Simulat. Modell. Pract. Theory (IF: 2.4), Elsevier, 2020.
C41 - Lazaros Toumanidis, Ryan Heartfield, Panagiotis Kasnesis, George Loukas, Charalampos Patrikakis. A Prototype Framework for Assessing Information Provenance in Decentralised Social Media: The EUNOMIA Concept. Proceedings of E-Democracy–Safeguarding Democracy and Human Rights in the Digital Age: 8th International Conference, e-Democracy 2019, Athens, Greece, December 12-13, 2019. Springer
C40 - A K M Mahtab Hossain, George Loukas. Participatory Location Fingerprinting through Stationary Crowd in a Public or Commercial Indoor Environment. Mobiquitous, EAI/ACM, November 2019.
C39 - Sakshyam Panda, Emmanouil Panaousis, George Loukas, and Christos Laoudias. Optimizing investments in cyber hygiene for protecting healthcare users. From Lambda Calculus to Cybersecurity Through Program Analysis. London, UK, September 19, 2019. Springer
J23 - Nikolaos Pitropakis, Emmanouil Panaousis, Thanassis Giannetsos, Eleftherios Anastasiadis, George Loukas. A Taxonomy and Survey of Attacks Against Machine Learning. Computer Science Review (IF: 5.4), Elsevier, 2019.
J22 - Dimitrios Kogias, Helen-Catherine Leligou, Michael Xevgenis, Maria Polychronaki, Evangelos Katsadouros, George Loukas, Ryan Heartfield, Charalampos Patrikakis. Towards a Blockchain-enabled Crowdsourcing platform. IT Professional, IEEE, 2019.
C38 - Md. Abdur-Rahman, George Loukas, Syed Maruf Abdullah, Areej Abdu, Syed Sadiqur Rahman, Elham Hassanain, Yasmine Arafa. Blockchain and IoT-based Secure Multimedia Retrieval System for a Massive Crowd: Sharing Economy Perspective (Demo). ACM ICMR, June 2019.
J21 - K. He, Y. Mao, J. Ning, K. Liang, X. Huang, E. Panaousis, G. Loukas. A new encrypted data switching Protocol: Bridging IBE and ABE without loss of data confidentiality. Access, IEEE, 2019. (IF: 3.6)
C37 - Nicole Huijts, Antal Haans, Sanja Budimir, Johnny Fontaine, George Loukas, Etienne Roesch, Anatolij Bezemski, Anne-Marie Oostveen, Wijnand IJsselsteijn. Users’ perceptions and responses to cyber-physical attacks on IoT devices in the home environment: A naturalistic field experiment. Society for Risk Analysis Benelux Conference, 25 March 2019.
J20 - Terry Brett, George Loukas, Yamir Moreno, Nicola Perra. The spreading of computer viruses on time-varying networks. Physical Review E 99, 050303, American Physical Society, 2019. (IF: 2.3)
J19 - Md. Abdur Rahman, M. Shamim Hossain, George Loukas, Elham Hassanain, Syed Sadiqur Rahman, Mohammed F. Alhamid, and Mohsen Guizani. Blockchain-based Mobile Edge Computing Framework for Secure Therapy Applications. Access, 6: 72469 - 72478, IEEE, 2018. (IF: 3.6)
J18 - George Loukas, Eirini Karapistoli, Emmanouil Panaousis, Panagiotis Sarigiannidis,
Anatolij Bezemskij, and Tuan Vuong. A taxonomy and survey of cyber-physical intrusion
detection approaches for vehicles. Ad Hoc Networks, Elsevier, 84: 124-147, 2019. (IF: 3.2)
J17 - Ryan Heartfield, George Loukas, Sanja Budimir, Anatolij Bezemskij, Johnny R. J. Fontaine, Avgoustinos Filippoupolitis, Etienne Roesch. A taxonomy of cyber-physical threats and impact in the smart home. Computers & Security, Elsevier, 78: 398-428, 2018. (IF: 2.7)
J16 - Ryan Heartfield, George Loukas. Detecting semantic social engineering attacks with the weakest link: Implementation and empirical evaluation of a human-as-a-security-sensor framework. Computers & Security, Elsevier, 76: 101-127, 2018. (IF: 2.7)
BC3 - Ryan Heartfield, George Loukas. Protection against semantic social engineering attacks in (editors: Mauro Conti, Gaurav Somani and Radha Poovendran) Versatile Cyber-security, Springer, 2018.
J15 – George Loukas, Tuan Vuong, Ryan Heartfield, Georgia Sakellari, Yongpil Yoon, Diane Gan. Cloud-based cyber-physical intrusion detection for vehicles using Deep Learning. Access, IEEE, 6: 3491 - 3508, 2018. (IF: 3.6)
BC2 - Silvio Sorace, Elisabeth Quercia, Ernesto La Mattina, Charalampos Z. Patrikakis, Liz Bacon, Georgios Loukas, Lachlan Mackinnon. Serious games: an attractive approach to improve awareness of community policing technologies. Springer Briefs in Policing, Springer, 2018.
C36 - CZ Patrikakis, DG Kogias, G. Loukas, A. Filippoupolitis, W. Oliff, SS Rahman, S. Sorace, E. La Mattina, E. Quercia. On the Successful Deployment of Community Policing Services: the TRILLION Project Case. IEEE International Conference on Consumer Electronics (IEEE ICCE), Las Vegas, 15 Jan. 2018.
J14 - Avgoustinos Filippoupolitis, William Oliff, Babak Takand, George Loukas. Location-Enhanced Activity Recognition in Indoor Environments using Off the Shelf Smart Watch Technology and BLE Beacons, Sensors, MDPI, 2017. (IF: 2.7)
C35 - William Oliff, Avgoustinos Filippoupolitis, George Loukas. Impact Evaluation and Detection of Malicious Spoofing Attacks on BLE Based Occupancy Detection Systems, International Conference on Internet of Things and Machine Learning (IML 2017), Liverpool, UK, 17-18 October 2017.
C34 - David Gresty, George Loukas, Diane Gan, Constantinos Ierotheou. Towards Web Usage Attribution via Graph Community Detection in Grouped Internet Connection Records, CEWE, CPSCom-2017, IEEE, Exeter, UK, 21-23 June 2017.
C33 - Anatolij Bezemskij, George Loukas, Diane Gan, Richard John Anthony. Detecting cyber-physical threats in an autonomous robotic vehicle using Bayesian Networks, CPSCom-2017, IEEE, Exeter, UK, 21-23 June 2017.
C32 - William Oliff, Avgoustinos Filippoupolitis, George Loukas. Evaluating the Impact of Malicious Spoofing Attacks on Bluetooth Low Energy Based Occupancy Detection Systems, IEEE SERA, London, UK, 7-9 June 2017.
C31 - Syed Sadiqur Rahman, Ryan Heartfield, William Oliff, George Loukas, Avgoustinos Filippoupolitis. Assessing the cyber-trustworthiness of human-as-a-sensor reports from mobile devices, IEEE SERA, London, UK, 7-9 June 2017.
C30 - Ryan Heartfield. George Loukas, Diane Gan. An eye for deception: A case study in utilising the Human-As-A-Security-Sensor paradigm to detect zero-day semantic social engineering attacks, IEEE SERA, London, UK, 7-9 June 2017.
J13 - Charalampos Z. Patrikakis and George Loukas. Wear it or share it? Wearables and Security. Cutter Executive Update, Cutter Information Corp., 2017.
J12 - Ryan Heartfield, George Loukas, Diane Gan. You are probably not the weakest link: Towards practical prediction of susceptibility to semantic social engineering attacks. Access, IEEE, 2016. (IF: 3.2)
C29 - Avgoustinos Filippoupolitis, Babak Takand, George Loukas. Activity Recognition in a Home Setting using Off the Shelf Smart Watch Technology. Smart ubiquitous technologies for human behaviour coaching (SUTCoaching), Granada, Spain, 14-16 Dec. 2016.
C28 - Anatolij Bezemskij, George Loukas, Richard Anthony, Diane Gan. Behaviour-based anomaly detection of cyber-physical attacks on a robotic vehicle. 8th International Symposium on Cyberspace Safety and Security (CSS), Granada, Spain, 14-16 Dec. 2016.
C27 - Avgoustinos Filippoupolitis, William Oliff, George Loukas. Bluetooth Low Energy based Occupancy Detection for Emergency Management. 15th International Conference on Ubiquitous Computing and Communications (IUCC), Granada, Spain, 14-16 Dec. 2016.
J11 - George Loukas, Yongpil Yoon, Georgia Sakellari, Tuan Vuong, Ryan Heartfield. Computation offloading of a vehicle's continuous intrusion detection workload for energy efficiency and performance. Simulat. Modell. Pract. Theory, Elsevier, 2016. (IF: 2.0)
C26 - Avgoustinos Filippoupolitis, William Oliff, George Loukas. Occupancy Detection for Building Emergency Management using BLE Beacons. ISCIS, Krakow, Poland, 27-28 Oct. 2016.
J10 - Ryan Heartfield and George Loukas. Predicting the performance of users as human sensors of security threats in social media. International Journal on Cyber Situational Awareness (IJCSA), ISSN (Print) 2057-2182, 2016.
J9 - George Loukas and Charalampos Patrikakis. Cyber and Physical Threats to the Internet of Everything. Cutter IT Journal, Cutter Information Corp, 29(7): 5-11, July 2016.
C25 - Anatolij Bezemskij, Richard John Anthony, George Loukas, Diane Gan. Threat Evaluation Based on Automatic Sensor Signal Characterisation and Anomaly Detection. The Twelfth International Conference on Autonomic and Autonomous Systems (ICAS 2016), IARIA, Lisbon, Portugal, June 26-30, 2016.
C24 - Ryan Heartfield and George Loukas. Evaluating the reliability of users as human sensors of social media security threats. Social Media, June 2016. [Best Paper Award]
J8 - David Gresty, Diane Gan, George Loukas, and Cos Ierotheou. Facilitating Forensic Examinations of Multi-User Computer Environments through Session-to-Session Analysis of Internet History. Digital Investigation, Elsevier, 16 (2016), S124-S133. (IF: 1.7)
J7 - R. Heartfield and G. Loukas. A taxonomy of attacks and a survey of defence mechanisms for semantic social engineering attacks. Computing Surveys (CSUR), ACM, 48(3), 2016. (IF: 6.7)
C23 - Tuan Vuong, George Loukas, Diane Gan, and Anatolij Bezemskij. Decision Tree-based Detection of Denial of Service and Command Injection attacks on Robotic Vehicles. 7th International Workshop on
Information Forensics and Security(IEEE WIFS 2015), IEEE, Rome, Italy, November 16-19, 2015.
C22 - Tuan Vuong, George Loukas and Diane Gan. Performance evaluation of cyber-physical intrusion detection on a robotic vehicle. 13th International Conference on Pervasive Intelligence and Computing (IEEE-PICOM 2015), IEEE, Liverpool, UK, October 26-28, 2015.
B3 - World Institute for Nuclear Security (co-author: George Loukas). Effectively Integrating Physical and Cyber Security. WINS International Best Practice Guide 4.11. May 2015.
B2 - George Loukas. Cyber-Physical Attacks: A growing invisible threat. 1st Edition. Butterworth-Heinemann (Elsevier), 2015.
C21 - Stelios Kapetanakis, Avgoustinos Filippoupolitis, George Loukas and Tariq Saad Al Murayziq. Profiling cyber attackers using case-based reasoning. 19th UK workshop on Case-Based Reasoning (UK-CBR 2014), Cambridge, UK, December 9, 2014.
C20 - David W. Gresty, Diane Gan and George Loukas. Digital Forensic Analysis of Internet History Using Principal Component Analysis. Proceedings of the 15th Annual Postgraduate Symposium on the Convergence of Telecommunications, Networking and Broadcasting (PGNet 2014), Liverpool, UK, June 23-24, pp. 237-242.
C19 - A. Filippoupolitis, G. Loukas and S. Kapetanakis. Towards real-time profiling of human attackers and bot detection. 7th International Conference on Cybercrime Forensics Education and Training (CFET), Canterbury, UK, 10-11 July 2014.
C18 - T. Vuong, A. Filippoupolitis, G. Loukas, D. Gan. Physical Indicators of Cyber Attacks Against a Rescue Robot. Proceedings of PerNEM, IEEE International Conference on Pervasive Computing and Communications (PERCOM), Budapest, Hungary, 24-28 March 2014.
J6 - R. Lent, G. Sakellari and G. Loukas. Strengthening the Security of Cognitive Packet
Networks. International Journal of Advanced Intelligence Paradigms (IJAIP), Inderscience, 6(1): 14-27, March, 2014.
J5 - G. Loukas, D. Gan and T. Vuong. A Review of Cyber Threats and Defence Approaches in
Emergency Management. Future Internet, MDPI, 5(2), pp. 205-236, 2013.
J4 - G. Sakellari and G. Loukas. A survey of mathematical models, simulation approaches and testbeds used for research in Cloud Computing. Simulat. Modell. Pract. Theory, Elsevier, http://dx.doi.org/10.1016/j.simpat.2013.04.002, 2013. (IF: 1.1)
BC1 - Lachlan MacKinnon, Liz Bacon, Diane Gan, Georgios Loukas, David Chadwick and Dimitrios Frangiskatos "Cyber Security Countermeasures to Combat Cyber Terrorism", in Babak Akhgar and Simeon Yates (eds), "Strategic Intelligence Management", Chapter 20, pp. 234-257, Butterworth-Heinemann (Elsevier), ISBN 978-0-12-407191-9, 2013.
C17 - G. Loukas, D. Gan and T. Vuong. A taxonomy of cyber attack and defence mechanisms for emergency management
networks. Proceedings of PerNEM, IEEE International Conference on Pervasive Computing and Communications (PERCOM), San Diego, CA, USA, 18-22 March 2013.
C16 - R. Heartfield and G. Loukas. On the feasibility of automated semantic attacks in the Cloud. Proceedings of IEEE ISCIS, pp. 343-351, ISBN 978-1-4471-4593-6, Paris, France, 3-5 October 2012.
C15 - D. Chadwick, D. Gan, G. Loukas, and D. Frangiskatos. Intensive
Teaching of cyber security for mid-career physical security professionals with limited academic background. 6th International Conference on Cybercrime Forensics Education and Training (CFET), Canterbury, UK, 6 September 2012.
J3 - G. Loukas and G. Oke. Protection Against Denial of Service Attacks: A Survey. Computer Journal, 53(7): 1020-1037, 2010 (IF: 1.0)
C14 - A. Filippoupolitis, G. Loukas, S. Timotheou, N. Dimakis, and E. Gelenbe. Emergency response systems for disaster management in buildings. NATO Symposium on C3I for Crisis, Emergency and Consequence Management, Bucharest, May 2009. [Best Paper Award]
C13 - S. Timotheou and G. Loukas. Autonomous Networked Robots for the Establishment of Wireless Communication in Uncertain Emergency Response Scenarios. Proceedings of the 2009 ACM Symposium on Applied Computing (SAC 09), pp. 1171-1175, Hawaii, USA, March 8 - 12, 2009
C12 - G. Loukas and S. Timotheou. Connecting trapped civilians to an ad hoc network of emergency response robots. 11th IEEE International Conference on Communications Systems (ICCS 2008), pp. 599-603, Guangzhou, China, November 2008
C11 - G. Loukas, S. Timotheou and E. Gelenbe. Robotic Wireless Network Connection of Civilians for Emergency Response Operations. 23rd IEEE International Symposium on Computer and Information Sciences, Istanbul, Turkey, October 27-29, 2008
C10 - G. Loukas, G. Oke and E. Gelenbe. Defending against Denial of Service in a Self-Aware Network: A Practical Approach. NATO Symposium on Information Assurance for Emerging and Future Military Systems. Ljubljana, Slovenia, October 13-14, 2008
C9 - G. Oke and G. Loukas. Distributed Defence Against Denial of Service Attacks: A practical view. Proceedings of the 2008 BCS International Conference on Visions of Computer Science, pp. 153-162, ISBN 978-1-906124-08-3, London, UK, 22-24 September 2008.
C8 - A. Filippoupolitis, L. Hey, G. Loukas, E. Gelenbe, and S. Timotheou. Emergency Response Simulation Using Wireless Sensor Networks. The 1st International Conference on Ambient Media and Systems, Quebec City, Canada, February 2008
C7 - A. Filippoupolitis, E. Gelenbe, D. Gianni, L. Hey, G. Loukas, and S. Timotheou. Distributed Agent-based Building Evacuation Simulator. Society for Modelling & Simulation, SCSC'08 conference, Edinburgh, Scotland, June 16-19, 2008
C6 - D. Gianni, G. Loukas, and E. Gelenbe. A Simulation Framework for the Investigation of Adaptive Behaviours in Largely Populated Building Evacuation Scenarios. International Workshop on "Organised Adaptation in Multi-Agent Systems" in the Seventh International Joint Conference on Autonomous Agents & Multi-Agent Systems (AAMAS 08), Estoril, Portugal, May 2008
J2 - G. Oke and G. Loukas. A Denial of Service Detector based on Maximum Likelihood Detection and the Random Neural Network. Computer Journal, 50(6):717-727, 2007 (IF: 1.3)
C5 - G. Loukas and G. Oke. A Biologically Inspired Denial of Service Detector Using the Random Neural Network. IEEE MASS2007, Bionetworks 07 workshop, Pisa, October 2007
C4 - G. Oke, G. Loukas, and E. Gelenbe. Detecting Denial of Service Attacks with Bayesian Classifiers and the Random Neural Network. Fuzz-IEEE 2007, London, July 2007
C3 - G. Loukas and G. Oke. Likelihood Ratios and Recurrent Random Neural Networks in Detection of Denial of Service Attacks. SPECTS 07, Security and Trust, San Diego, July 2007
J1 - E. Gelenbe and G. Loukas. A Self-Aware Approach to Denial of Service Defence. Computer Networks, 51(5):1299-1314, April 2007(IF: 1.3)
B1 - George Loukas. Defence Against Denial of Service in Self-Aware Networks. PhD thesis, Imperial College, University of London, 2006.
C2 - E. Gelenbe, M. Gellman, and G. Loukas. An Autonomic Approach to Denial of Service Defence. IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, pp. 537-541, June 2005
C1 - E. Gelenbe, M. Gellman, and G. Loukas. Defending Networks against Denial of Service Attacks. Conference on Optics/Photonics in Security and Defence (SPIE), Unmanned/Unattended Sensors and Sensor Networks, vol. 5611, pp. 233-243, October 2004
Reviewer for:
Journals
ACM Transactions on Internet Technology, Communications of the ACM, IEEE Transactions on Dependable and Secure Computing, IEEE Journal on Selected Areas in Communications, IEEE Transactions on Network and Service Management, IEEE Transactions on Parallel and Distributed Systems, IEEE transactions on Systems, Man and Cybernetics, IEEE Access, Elsevier Vehicular Communications, Elsevier Ad Hoc Networks, Elsevier Performance Evaluation, Elsevier Journal of Computational Science, Elsevier Simulation Modelling Practice and Theory, Elsevier Journal of Network and Computer Applications, BCS Computer Journal, Springer Journal of Internet Services and Applications, MDPI Future Internet, MDPI Sensors, MDPI Information, MDPI Entropy, Wiley International Journal of Network Management
Conferences
IEEE International Conference on Pervasive Computing (PERCOM), IEEE International Conference on High Performance and Communications (HPCC), IEEE International Symposium on Computer and Information Sciences (ISCIS), IEEE International Conference on High Performance Computing (HIPC), IEEE / ACM International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems (MASCOTS), IEEE Global Communications Conference (GLOBECOM), IEEE Wireless Communications and Networking Conference (WCNC), IEEE Consumer Communications & Networking Conference (CCNC), International Conference on Algorithms and Architectures for Parallel Processing (ICA3PP), International Conference on Future Internet of Things and Cloud (FiCloud), Next Generation Internet Networks (NGI), International Conference on Artificial Neural Networks (ICANN), IAES International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), International Conference on Telecommunications (ICT).
 A cyber-physical system is vulnerable where cyber and physical spaces overlap, as attacks lead to physical actions inconsistent with system states and goals. Monitoring its physical characteristics improves threat detection accuracy and reduces detection latency.
A cyber-physical system is vulnerable where cyber and physical spaces overlap, as attacks lead to physical actions inconsistent with system states and goals. Monitoring its physical characteristics improves threat detection accuracy and reduces detection latency. We have introduced the paradigm of detecting security threats by empowering users to act as human sensors. HaaS breaks away from the tradition of system-specific technical security measures and challenges the misconception that users are the weakest link. People are invaluable threat detectors in their organisations, especially for deception-based threats that defeat technical security measures.
We have introduced the paradigm of detecting security threats by empowering users to act as human sensors. HaaS breaks away from the tradition of system-specific technical security measures and challenges the misconception that users are the weakest link. People are invaluable threat detectors in their organisations, especially for deception-based threats that defeat technical security measures.



 gre.ac.uk, +44 (0)20 8331 9612, Room QM365, University of Greenwich, Old Royal Naval College, SE10 9LS, UK
gre.ac.uk, +44 (0)20 8331 9612, Room QM365, University of Greenwich, Old Royal Naval College, SE10 9LS, UK